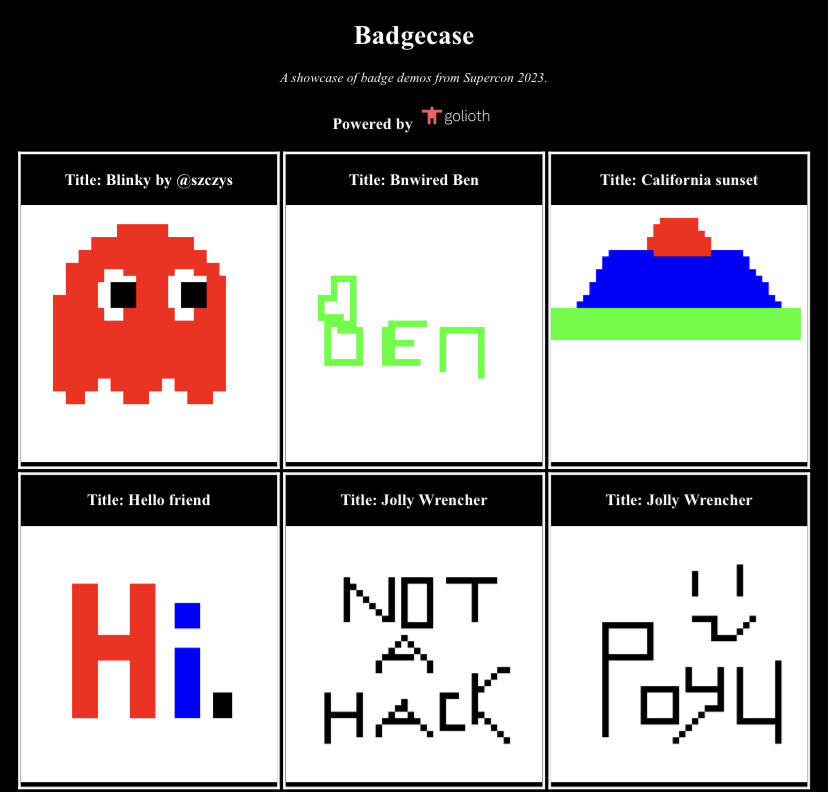
Screenshot of Badgecase gallery page.
The final day of Supercon 2023 had more great talks, including an incredible recollection of Restoring the Apollo Guidance Computer. However, the real highlight was seeing all of the various badge hacks starting to take their final form, ultimately culminating with the Badge Hacking Ceremony at the end of the day.
Mike and I had made enough progress on Saturday after pivoting away from our PIO / DMA exploits that the remaining work on Sunday morning primarily revolved around final hardware setup and managing DNS records (riveting stuff I know!). It was important for us to get this done early, because our demo involved attendee participation. After about an hour, badgecase.io was officially live!
Badgecase works by taking the pixel data from the sketching application
mentioned in yesterday’s
post, delivering it over
I2C to an nRF9160 on an Aludel
Mini dev
board
(designed by our coworker and Supercon O.G. Chris
Gammell), which sends it up as
CBOR CoAP
payloads to Golioth. From there, the Badgecase backend, a
Rust
tokio-rs/axum webserver I had been hacking
on throughout the weekend, receives the data from Golioth over
websockets,
decodes it, renders a PNG, and uploads it to a Google Cloud
Storage bucket. When requests are made to
badgecase.io or
supercon23.badgecase.io, the same application
renders HTML that displays a gallery of all images in the bucket.
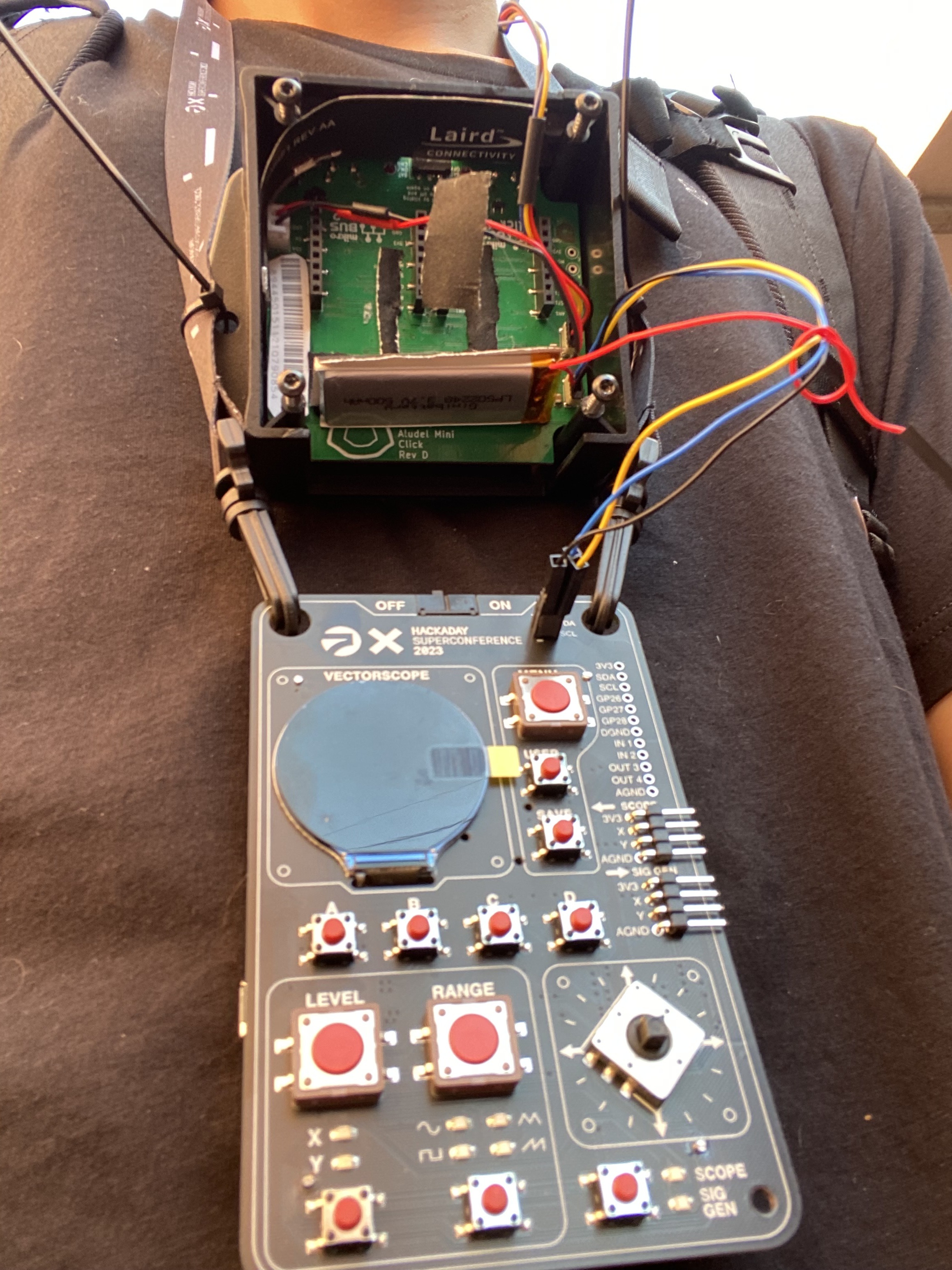
Our full hardware setup.
There were a few interesting optimizations, both for performance and speed of development, that we made throughout building the demo. First, because many of the images contained primarily white background pixels, we opted to only send color pixels up to Golioth. In addition, Mike was able to pack the x and y coorindates, as well as the color, into a 16-bit integer. Because we were working with a 40x40 pixel canvas, we needed 6 bits each for the x and y values, which left us with 4 bits for color encoding. The sketch application only supported white, black, red, green, and blue, so 4 bits was more than enough.
XXXXXX XXXXXX XXXX
x y c
Nevertheless, with more detailed sketches, we were unable to stuff all of the data into a single CoAP message, so points were fragmented across multiple messages, with the first providing metadata including the total number of expected points. Also tucked in that metadata was the name of the sketch, which was picked by the author and delivered to the nRF9160 prior to sending the pixel data via a Golioth Remote Procedure Call (RPC).
On the backend, these fragmented points were re-assembled, and used to encode a
PNG image using the Rust image crate. The
name of the sketch, and a unique ID that was generated on the device and
included in the first message’s metadata, were used to form a name for the image
when uploading to the bucket. On each request for
badgecase.io, the HTML page was rendered by
listing all objects in the bucket, parsing the names for metadata, and passing
it to a handlebars template engine. While I would
not recommend using a blob storage bucket as your database, doing so minimized
the dependencies of the application. Furthermore, because
badgecase.io is running on Google Cloud
Run, authorizing access from the container to the
bucket was seamless.
In between attending talks and having impromptu conversations with other attendess, Mike and I were able to collect a small gallery of sketches that folks at the conference, and those following at home, could see updating in real time. By the end of the day, we here able to show off a demo that included images from many of the attendess in the audience. It is worth watching the entire badge hacking ceremony as ours was just one in a fascinating display of creativy and engineering.
Outside of our Badgecase shenanigans, a few personal highlights from Day 3 for me included meeting Tom Verbeure and Time “mithro” Ansell. I have been following both of these folks for quite some time, and their work and writing has been a huge inspiration for me as I have explored FPGAs and chip design. Tim was also nice enough to give me a Fomu!

The Fomu!
Meeting both of them, as well as getting to have an extended conversation with Matt Venn of TinyTapeout fame the day before, was an incredible opportunity, and I hope the work that I do will someday have a similar level of impact. The other highlight was getting to spend the weekend hacking with Mike. He did so much to make my first Supercon an awesome experience for me, and I’m grateful to work with awesome folks like him.

Mike and I in front of the add-on wall.
For now, after experiencing the true wonder of Hackaday Supercon, I’m off to RISC-V Summit for even more hardware goodness. If you’ll be there and want to chat, feel free to reach out via one of the social links on the homepage!